
Attacks Keep Rising as Threat Shows its Resilience
February 25, 2025
How to build a strategy for your unstructured data and AI storage needs
February 25, 2025Quantum-Safe Encryption: Safeguarding Data for the Quantum Era
Industry Trends
In today’s ever-evolving cybersecurity landscape, staying ahead of potential threats is a constant challenge. Advanced persistent threats, ransomware, and wipers are just a few risks organizations must guard against. However, quantum computing is one of the most complex and far-reaching challenges on the horizon. While not an immediate threat, “collect now, decrypt later” underscores the urgency of preparing for a future where current cryptographic standards may be rendered obsolete.
Thanks to their ability to perform complex calculations exponentially faster than classical computers, quantum computers promise to revolutionize many scientific fields, such as chemistry, physics, and materials science. However, they also pose a significant risk in the wrong hands—potentially breaking today’s encryption methods and exposing sensitive data to malicious actors.
The Threat to Traditional Encryption
Current encryption protocols such as RSA and ECC (used in HTTPS, SSH, and IPsec VPNs) rely on the difficulty of factoring large numbers or solving discrete logarithm problems for security. However, quantum computers using advanced methods like Shor’s algorithm could efficiently solve these problems, leaving traditional encryption methods vulnerable to attack.
A sufficiently powerful quantum computer capable of breaking modern encryption is unlikely to be available within the next 8–10 years, although even that time is decreasing with each innovation. The issue is that adversaries are already collecting and storing sensitive data for future decryption. This highlights the need for proactive measures to safeguard information against post-quantum threats.
Preparing for the Quantum Future
As organizations recognize the risks posed by quantum computing, the need to adopt quantum-safe encryption strategies has never been more urgent. Concerns over eavesdropping on undersea fiber optic cables and other data interception techniques, for example, reinforce the necessity of securing communication channels now against future quantum threats.
Quantum-safe encryption, or post-quantum cryptography, refers to cryptographic protocols designed to resist these quantum attacks. Unlike traditional encryption, which depends on computational complexity, quantum-safe encryption is rooted in mathematical problems believed to be insurmountable even for quantum computers. Examples include lattice-based cryptography, hash-based cryptography, and multivariate polynomial cryptography.
Quantum-Safe Encryption Strategies
To counteract these threats, organizations must adopt quantum-safe encryption techniques that can withstand quantum computing advancements. Three major approaches are being explored today:
- Quantum Key Distribution (QKD): Leverages quantum mechanics to securely distribute symmetric encryption keys in an untrusted environment
- Quantum-Safe Encryption: Uses proprietary techniques to ensure a secure key exchange resistant to quantum attacks
- Post-Quantum Cryptography (PQC): Implements new cryptographic algorithms believed to be difficult for quantum computers to solve, such as lattice-based encryption
Fortinet has already introduced quantum-safe security solutions, including integrating the NIST Post-Quantum Encryption (PQC) CRYSTALS-KYBER algorithm in FortiOS 7.6. However, this discussion focuses on QKD and its role in securing future communications.
Introduction to Quantum Key Distribution
QKD ensures that communication security is based on the laws of physics, which are immutable. As famously stated by Chief Engineer Scotty in Star Trek, “Ye cannae change the laws of physics.”
QKD uses principles from quantum mechanics, such as quantum entanglement, Heisenberg’s uncertainty principle, and the no-cloning theorem. QKD exploits these fundamental attributes of quantum mechanics:
- A quantum key in the form of entangled qubits can exist at two places at the same point in time.
- Any attempt to measure a qubit alters the characteristic information of qubits at both places and can immediately be identified. This also implies that a qubit cannot be copied.
In cryptography terms, these entangled quantum particles or qubits are encoded with cryptographic keys and transmitted between a sender (Alice) and a receiver (Bob). If an eavesdropper (Eve) attempts to intercept these particles, their quantum states will be disturbed, alerting Alice and Bob instantaneously to the presence of an intruder. This fundamental principle of quantum mechanics ensures that any attempt at unauthorized interception is immediately detected.
The observant reader might ask, “How can this quantum state change occur instantaneously in two places potentially many miles apart? Wouldn’t that require faster-than-light travel?” This is the Spooky Action at a Distance that got Einstein so annoyed in his letter to Max Born.
“I cannot seriously believe in it because the theory cannot be reconciled with the idea that physics should represent a reality in time and space, free from spooky action at a distance.”
Albert Einstein, The Born-Einstein Letters, 1947
This is just one of the weird behaviors of quantum mechanics that you must accept, even if the method is not completely understood.
Real-World QKD Implementation
Despite its theoretical promise, QKD faces challenges related to scalability, transmission distance, and integration with existing infrastructure. However, ongoing research and technological advancements are steadily overcoming these hurdles.
A recent real-world demonstration by JPMorgan Chase (JPMC) showcased quantum-safe high-speed 100 Gbps site-to-site IPsec tunnels secured using QKD. The test was conducted between two JPMC data centers in Singapore, covering over 46 km of telecom fiber, and achieved 45 days of continuous operation.
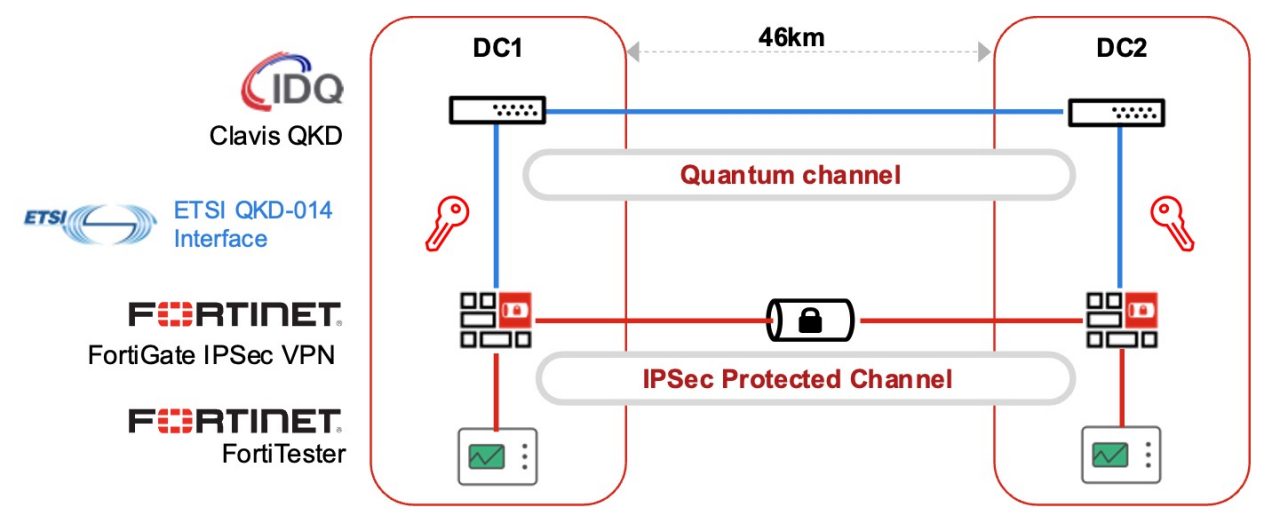
Two different VPN configurations were tested:
- A single QKD-secured VPN tunnel with a maximum throughput of 80 Gbps
- A multi-VPN tunnel configuration featuring 12 QKD-secured VPN tunnels, each with 8.39 Gbps throughput, resulting in a total of 99.62 Gbps across all tunnels
The network leveraged QKD vendor ID Quantique for the quantum key exchange, Fortinet’s FortiGate 4201F for network encryption, and FortiTester for performance measurement.
The Race for Quantum-Safe Solutions
In response to the looming threat of quantum computing, the global cybersecurity community has been actively developing quantum-safe encryption standards. The National Institute of Standards and Technology (NIST) has spearheaded the Post-Quantum Cryptography Standardization project to evaluate and standardize quantum-resistant algorithms. Through rigorous selection and cryptographic analysis, NIST is paving the way for the widespread adoption of quantum-safe encryption.
However, transitioning from traditional encryption to quantum-safe solutions presents challenges, including interoperability, performance impact, and backward compatibility. Organizations must carefully assess their cryptographic infrastructure and create a roadmap for migration to quantum-resistant encryption.
Protecting Today’s Data Against Tomorrow’s Threats
As cyberthreats continue to evolve, ensuring the long-term security of sensitive information is paramount. Quantum-safe encryption offers a proactive approach to mitigating quantum risks and securing critical data against future decryption attacks.
By investing in quantum-safe solutions today, organizations can future-proof their cryptographic infrastructure, ensuring resilience in the face of rapid technological advancements. While the transition to quantum-safe encryption is complex, the benefits of securing sensitive data far outweigh the costs.
It Takes a Village
By harnessing the power of quantum-resistant cryptographic algorithms and advancing QKD technologies, we can secure our data against the threats of the quantum era. But no single entity can tackle this challenge alone. The shift toward quantum-safe encryption is a collaborative effort requiring input from researchers, policymakers, and industry leaders.
But the challenge is clear. As quantum computing continues to develop, the time to act is now. Ensuring data security for the future demands a collective commitment to innovation, standardization, and the adoption of quantum-safe encryption practices. Together, we are paving the way for a future where data security transcends the bounds of classical computing, ushering in a new era of quantum-safe communications and cryptography.